下一站江湖2峰顶怪人流程介绍
时间:2025-09-23 | 作者: | 阅读:242下一站江湖2峰顶怪人流程介绍?也许有的伙伴还不了解下一站江湖2峰顶怪人任务怎么做,下面由心愿游戏小编为您介绍一下吧,一起来看看哦。
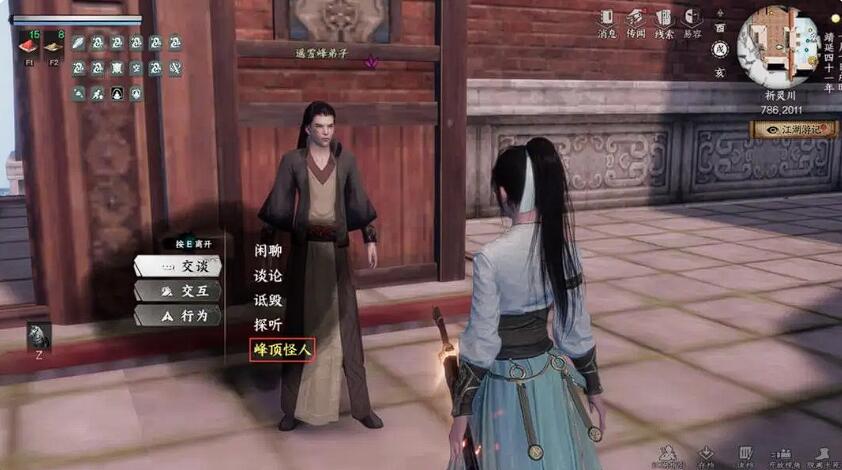
要触发峰顶怪人任务,首先需前往遥雪峰地图坐标(786.2011)。到达该位置后,会看到一名身着棕色道袍的遥雪峰弟子在平台上巡逻,靠近后与其对话即可接取任务。注意此任务无等级限制,但建议先提升轻功等级至3级以上,以便应对后续的地形探索。
与弟子对话后,任务会要求你寻找散落在遥雪峰各处的”寒铁碎片“。这些碎片共有3处刷新点:第一处位于(792.2005)的巨石缝隙中,需打破岩石获取。
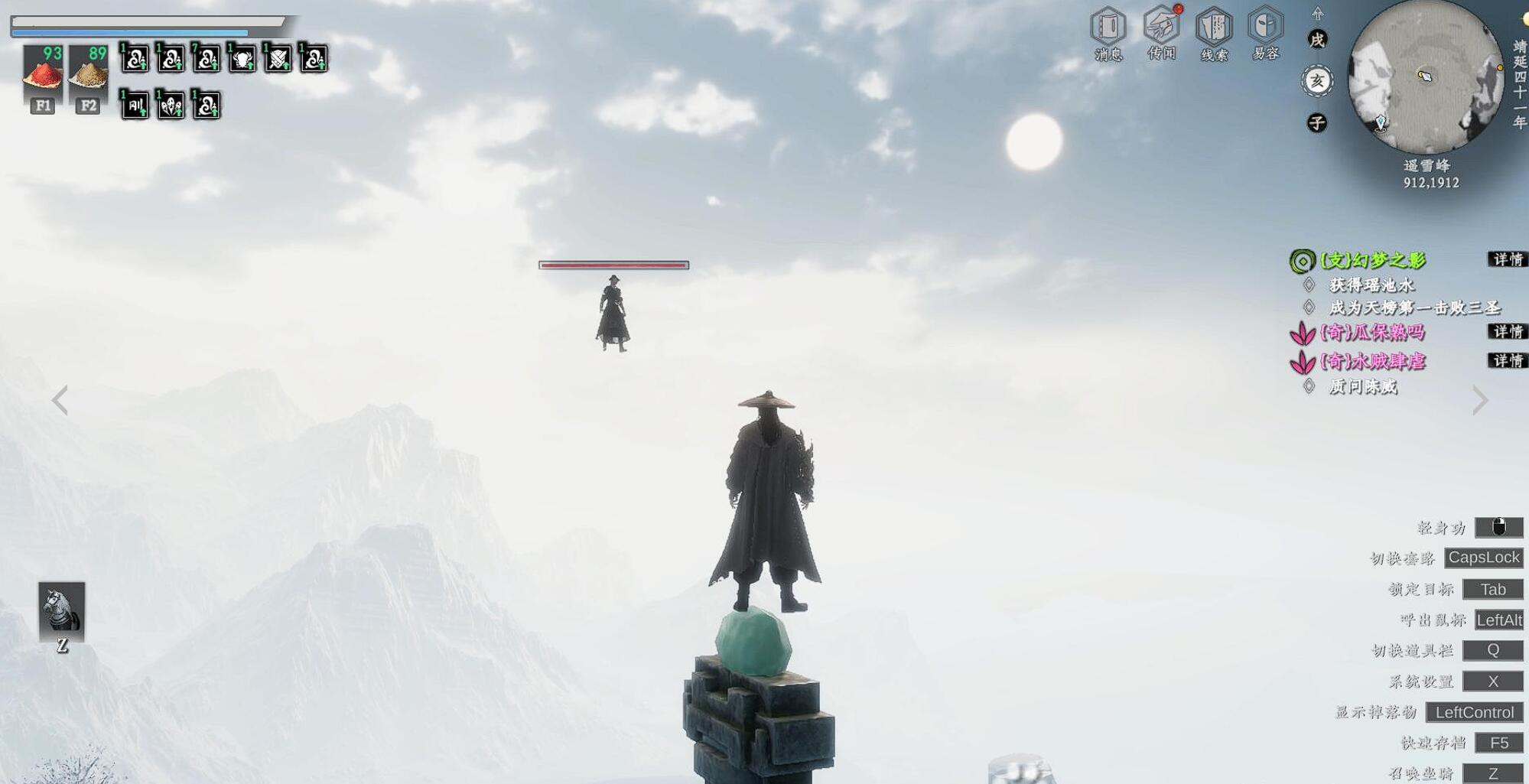
第二处在(780.2018)的雪堆里,使用火把融化积雪即可发现。第三处藏在(795.2022)的悬空平台上,需借助二段跳才能到达。收集齐碎片后自动合成”寒铁钥匙“。带着钥匙返回初始接取任务的弟子处,他会指引你前往峰顶洞穴。进入洞穴后直走到底,使用钥匙开启冰门,即可见到峰顶怪人。
来源:https://www.wandoujia.com/apps/8313464/15751680141473441973.html
免责声明:文中图文均来自网络,如有侵权请联系删除,心愿游戏发布此文仅为传递信息,不代表心愿游戏认同其观点或证实其描述。
相关文章
更多-
- 下一站江湖2最强剑武器
- 时间:2025-12-29
-

- 下一站江湖2福缘怎么提升
- 时间:2025-11-25
-

- 下一站江湖2万法森罗怎么获取
- 时间:2025-11-21
-
- 下一站江湖2神兵图鉴:顶级装备获取与养成全解析
- 时间:2025-07-29
-

- 《下一站江湖2》响马铃使用攻略
- 时间:2025-07-26
-
- 《下一站江湖2》感悟作用介绍
- 时间:2025-07-26
-
- 《下一站江湖2》朔海派玩法介绍
- 时间:2025-07-26
-

- 《下一站江湖2》玉沙关地宫玩法介绍
- 时间:2025-07-26
精选合集
更多大家都在玩
大家都在看
更多-
- 甜心格格第19集剧情介绍
- 时间:2026-02-11
-

- 明日方舟:终末地武器基质攻略
- 时间:2026-02-11
-

- 钟和龚姓网名大全男生(精选100个)
- 时间:2026-02-11
-
- 甜心格格第17集剧情介绍
- 时间:2026-02-11
-
- 键盘设置快捷键怎么设置
- 时间:2026-02-11
-
- 甜心格格第15集剧情介绍
- 时间:2026-02-11
-
- 拉翔是什么意思
- 时间:2026-02-11
-

- 希沃白板如何恢复误删除课件?希沃白板恢复误删除课件的方法
- 时间:2026-02-11